The CryptoLocker Virus And How To Secure Your PC From It
One of the dangerous malware that targets Microsoft Windows is CryptoLocker. This is a ransomware Trojan that first appeared in September 2013. It has gained worldwide fame as it has wreaked havoc in thousands of computers across the globe. This is a malware that literary kidnaps and holds the data in your computer ransom once it has taken over your system. If you choose not to pay the ransom, the data is deleted permanently.
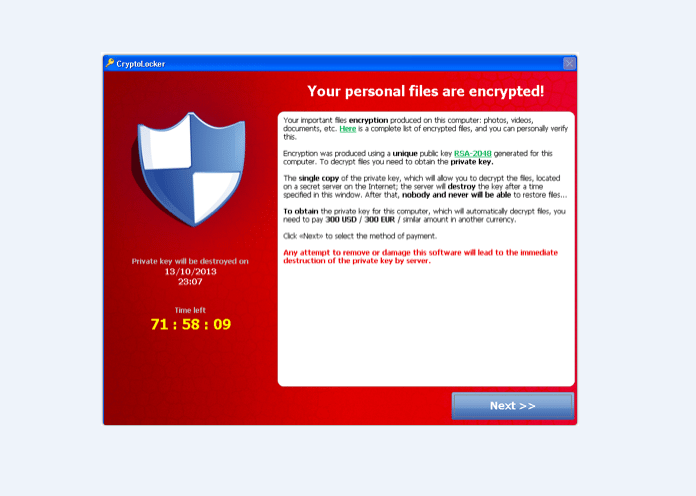
CryptoLocker at Work
Propagation is via email attachments that are infected or through existing botnets. The malware gets activated after which it uses RSA public-key cryptography to encrypt certain files on the computer’s local drives as well as on the network drives mounted using a private key that is hidden within the control servers of the malware.
What follows is a request or rather a threat asking you to pay a ransom either as a pre-paid cash voucher or bitcoin within a fixed deadline if you wish to obtain the key to decrypt the data. After the set period elapses, the malware deletes the private key. After this period, the data can only be decrypted after paying a significantly higher price to the online service provided by the malware’s operator.
For a business, data is highly valuable and an asset that they can’t afford to lose. Sometimes paying the ransom seems like the only way out. However even after paying the ridiculous sum demanded, some victims have reported that the data was never decrypted.
Removing the CryptoLocker is not very difficult. Nonetheless, the files that were encrypted remain encrypted, and researchers say it is almost impossible to break. Keep in mind that we here at Computer Fixperts can remove your computer virus at your home or office. We offer same day computer repairs in Brisbane.
Stopping CryptoLocker
Turn the computer on and off won’t work to remove CryptoLocker. Tinkering with the hardware components won’t help either. The developers of CryptoLocker also made it so that it blocks all common troubleshooters. CryptoLocker actually makes changes to the computer’s registry each time the computer is restarted. Remote access of the drive is also futile because the malware encrypts data on both fixed and remote drives.
It, therefore, seems that with no data recovery solution you are left with only one option which is to follow the hacker’s instructions. However, even then there’s a possibility that you still won’t get access to your files. Remember that the virus will still be infecting your system and may strike again.
The Good News
In August 2014 Fox-IT working alongside FireEye developed an online service through which infected users could retrieve the private key for decryption. Users did this by uploading a sample file and then receiving a decryption tool.
Mitigating CryptoLocker
CryptoLocker may go undetected by security software especially if it is a new superior version. However, if infection is suspected, immediate removal which is quite simple should be started. All infected computers should be disconnected from the network. Also all online account passwords and network password should be changed.
Above all things, in case you suspect that you have been hit with a CryptoLocker malware attack you should get immediate professional help.
YouTube Link
